
Crypto Security: Protect Your Coins and NFTs From Being Stolen
With crypto prices in free fall, crypto firms laying off thousands of workers and coins that are considered "stable" losing all their value, it's more important than ever to secure your remaining portfolio.
The current crypto crash isn't the only way people are losing their money. There have been an increasing number of scams that give thieves access to your accounts and crypto assets. Just recently in May, Seth Green had several NFTs worth over $300,000 stolen, after the actor connected his crypto wallet to a scam website pretending to be a credible NFT project.
Protecting your crypto means taking some of the same steps you'd use to safeguard your other digital accounts, such as creating and using strong passwords. However, crypto accounts have unique characteristics like seed phrases that require additional security. Also, the crypto industry still lacks the regulatory framework necessary for the retrieval of your crypto assets if they're stolen.
In this story, we'll cover several ways you can protect your cryptocurrency and NFTs from being purloined and explain why it's worth taking the time to properly secure your digital assets from being stolen. For more on crypto, learn five questions every investor should ask about cryptocurrency and the latest details on bitcoin's wild price swings.
Always follow these two basic password security rules
One of the easiest ways to protect your digital assets is with strong passwords. Ideally, you want your passwords to be at least eight characters long and include random capital letters, numbers and other special characters. If you can make your password longer, however, you should, because the longer the password, the harder it is to crack, in theory.
If you're worried about remembering all of your long, complicated and unique passwords, consider using a password manager, which makes it simple and secure to store and use your passwords from one place. We recommended choosing a password manager with encrypted storage and two-factor authentication for extra security.
Also, when creating an account, never repeat your passwords. If one of your accounts is compromised, your others will also be at risk.

A strong password is vital to keeping your digital assets secure.
James Martin/CNETUse a hardware crypto wallet for your most treasured assets
Your crypto wallet serves as the gateway to your crypto assets. "Hot" wallets such as software or mobile apps operate online, while "cold" wallets are hardware devices that work offline. Crypto wallets don't hold the actual coins or tokens -- they store the private keys that prove you own your crypto assets and let you buy, sell or trade on blockchains.
Anytime you purchase cryptocurrency or NFTs, they must be stored somewhere. Most people keep their assets in a digital wallet or marketplace, such as Coinbase or MetaMask, because they're free and easy to use, but for your most valuable holdings, you may want to consider a physical wallet.
A hardware, or cold, wallet allows you to store cryptocurrency and NFTs on a physical drive, which you can connect to a computer to access. Hardware wallets are generally more difficult to hack into, so they're a preferred option when storing digital assets that are especially high in value.

The Trezor One hardware wallet ($48.49) works with bitcoin, ethereum, litecoin and a variety of other cryptocurrencies.
TrezorHere's more on the different types of crypto wallets.
Keep the seed phrase for your crypto wallet secure and offline
In addition to a password, most crypto wallets use a seed phrase for additional security. This seed phrase acts like a master password and is created whenever you set up a new wallet. A seed phrase is made up of 12 or 24 words that you can use to sign in to your account on other devices, or recover your account if you forget your password.
While this seed phrase provides additional security, it also comes with risk -- anyone who learns your seed phrase could potentially steal all the crypto assets recorded in your wallet. While you might be tempted to store your seed phrase somewhere online, it's crucial to write it down -- offline -- to prevent anyone from accessing it.
Once you write down your seed phrase, store it in a safe or lockbox, so that it's not easy for anyone else to access. Specialized seed phrase hardware tools, like Cryptosteel and Crypt Keeper, can securely store your 12 or 24 words in a portable system that's protected from fire and flooding.
If your seed phrase is either lost or stolen, but you still know your password, immediately log in to your wallet and generate a brand new seed phrase.
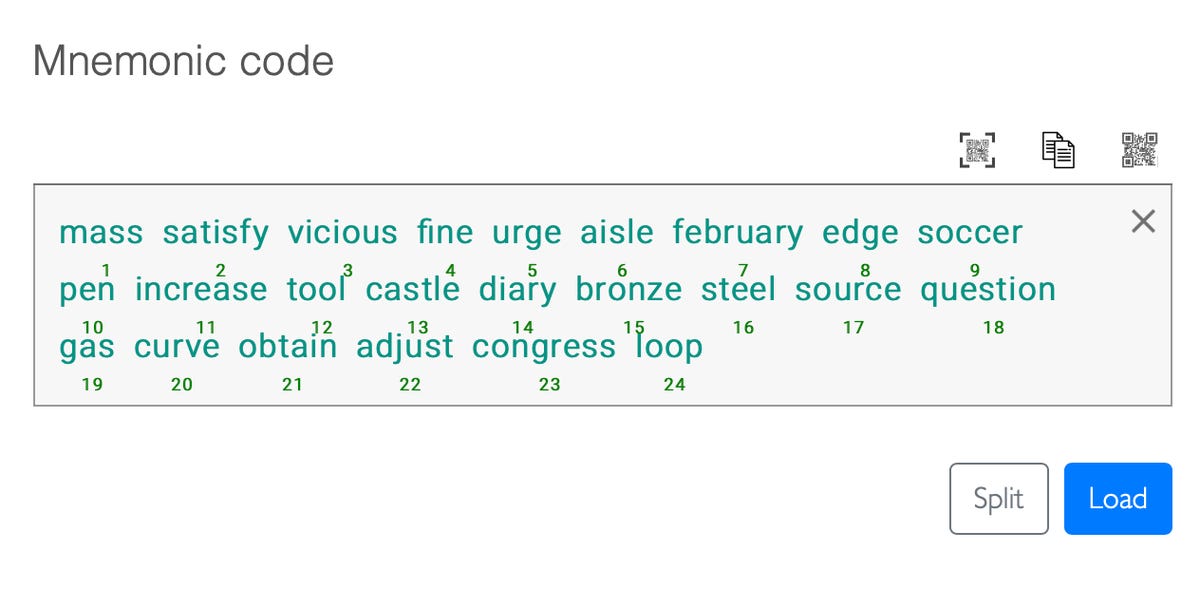
This is an example of a randomly created 24-word seed phrase.
Nelson Aguilar/CNETBe wary of frauds in direct messages on Discord
Discord is one of the unofficial homes of crypto and NFT communities. It's where many crypto enthusiasts go to discuss upcoming NFT projects, cryptocurrency prices, real-life events and even personal lives. Fans of NFT projects use Discord to form communities -- but it's also where hackers and thieves go to compromise accounts.
Here's how it works: A hacker may directly message you, pretending to be part of a project that you're following and interested in. The DM looks official and usually claims that you can mint an NFT that's difficult to get, at a relatively cheap price, and includes a link to follow. But when you click the link, connect your wallet and attempt to purchase the NFT, your wallet is drained of all your NFTs and crypto. And there's really no way to get it all back.
The most important research you can do to avoid falling for a fake NFT website is to use verified channels to find the correct website when attempting to mint or purchase a newly created NFT. Even if you receive a link from what seems like a credible source, use multiple online sources like Google, Twitter and Opensea to verify that you have the correct URL for the project.
An even simpler method to avoid falling into a scam is to disable DMs on Discord. On your mobile device, launch the Discord app, tap your profile picture on the bottom right, go into Privacy & Safety, and toggle off Allow Direct Messages From Server Members. You'll no longer receive direct messages on Discord.
Discord is where people go to discuss cryptocurrency and NFTs, as well as prey on potential victims.
DiscordDon't fall for support scams on Twitter
Like Discord, Twitter is a hunting ground for hackers looking to swindle unsuspecting victims into giving away their assets.
On Twitter, anytime someone mentions "stolen account," "lost password" or even "MetaMask," an army of hackers may respond, offering to help recover stolen assets or restore access into accounts. Hackers may then ask for your seed phrase via DM and use it to steal your crypto or NFTs.
If you need support, go straight to the official customer service site on Twitter. Never give anyone your seed phrase, ever, even if an account is verified -- sometimes hackers have access to verified accounts. And never share your screen.

Not even Elon Musk can stop these Twitter scammers.
James Martin/CNETFor more about cryptocurrency security, learn whether it's possible to insure bitcoin and how the Securities and Exchange Commission is taking on crypto fraud.
Source




